Alessio Casta
- 3 min read
The Rise of AI in Cybersecurity: Revolutionising Protection

In today’s digital landscape, with the relentless advancement of cybercriminals' methods, conventional cybersecurity strategies often fall behind. Yet, there is a transformative factor emerging: Artificial Intelligence (AI). AI shines as a formidable force in cybersecurity due to its capacity to process extensive datasets, discern intricate patterns, and adjust instantaneously, making it an invaluable asset in combating online threats.
Understanding the Role of AI in Cybersecurity
At its core, cybersecurity is about staying one step ahead of malicious actors. This requires not only robust defences but also proactive strategies to anticipate and mitigate potential threats. AI excels in this regard by leveraging machine learning algorithms to detect anomalies, recognize patterns, and predict potential security breaches.
One of the key advantages of AI in cybersecurity is its ability to handle vast amounts of data with speed and accuracy. By analysing historical data and real-time network activity, AI algorithms can identify deviations from normal behaviour, flagging suspicious activities that might go unnoticed by human operators.
Furthermore, AI can adapt and learn from new threats in real-time, continuously improving its ability to detect and respond to emerging cyber threats. This adaptive capability is crucial in an environment where cyber threats are constantly evolving, making traditional signature-based approaches less effective.
Implementation of AI in Cybersecurity Systems
Let's take a closer look at how AI is implemented in various cybersecurity systems:
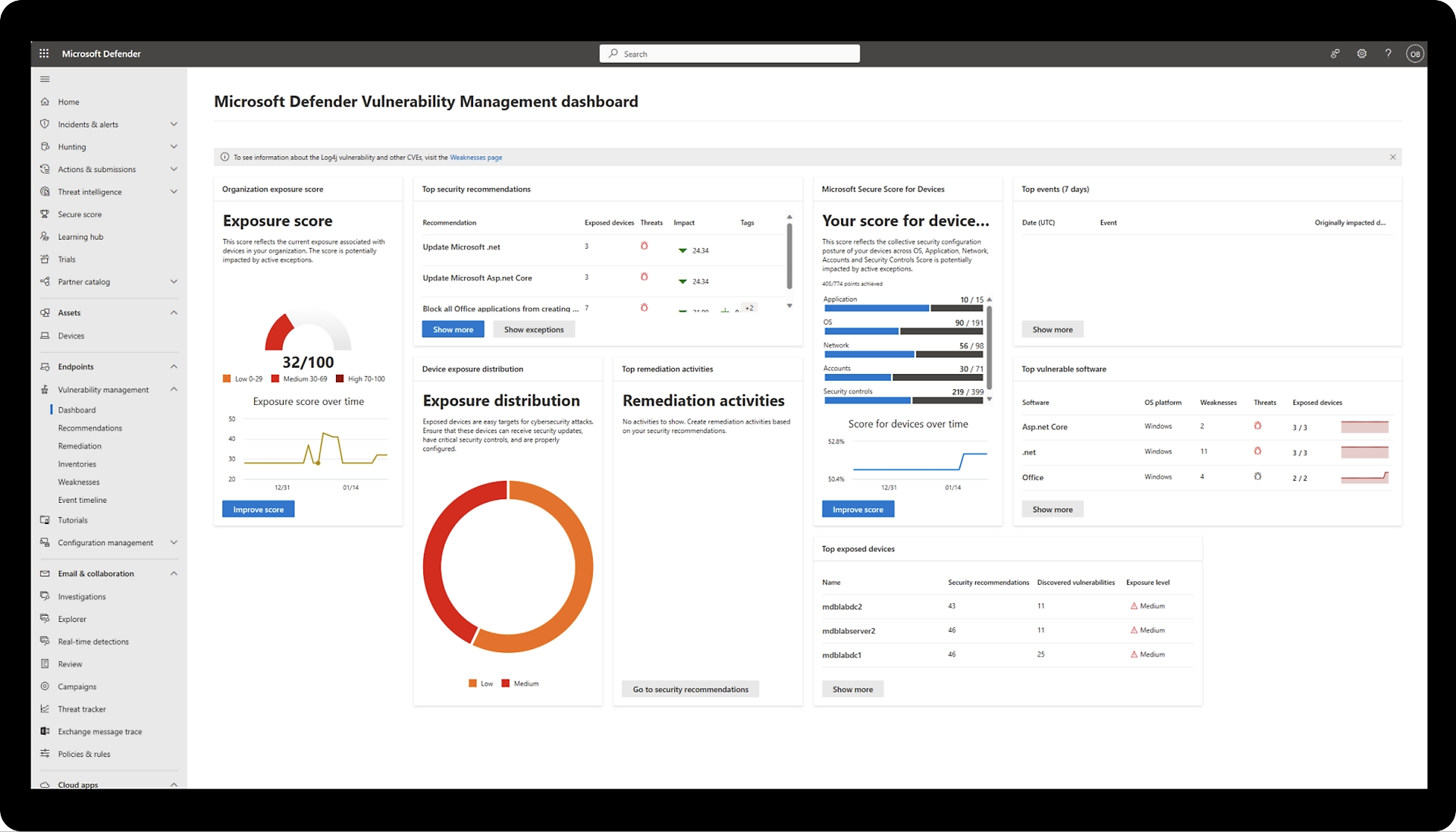
- Threat Detection and Prevention: AI-powered threat detection systems monitor network traffic, endpoints, and applications for any unusual behaviour or indicators of compromise. These systems can identify potential threats such as malware, phishing attempts, and insider threats in real-time, allowing for immediate action to be taken to mitigate the risk.
- Behavioural Analytics: AI algorithms analyse user behaviour to establish a baseline of normal activity. Any deviations from this baseline are flagged as suspicious and investigated further. This approach helps detect insider threats, unauthorized access attempts, and other anomalous activities that traditional security measures might miss.
- Vulnerability Management: AI-driven vulnerability management systems scan networks and applications for potential security vulnerabilities. By analysing code, configurations, and system architecture, these systems can identify weaknesses that could be exploited by attackers. Additionally, AI can prioritise vulnerabilities based on risk severity, helping security teams focus their efforts on the most critical issues.
- Automated Response: AI can automate response actions to security incidents, enabling faster containment and mitigation of threats. For example, AI-powered incident response platforms can isolate compromised systems, block malicious traffic, and apply patches or updates to vulnerable software automatically.
- User Authentication: AI-enhanced authentication systems use biometric data, behavioural analysis, and contextual information to verify users' identities more accurately. This reduces the risk of unauthorized access and strengthens overall security posture.
Microsoft Leaning In
Microsoft Copilot for Security is a generative AI-powered security solution that helps increase the efficiency and capabilities of defenders.
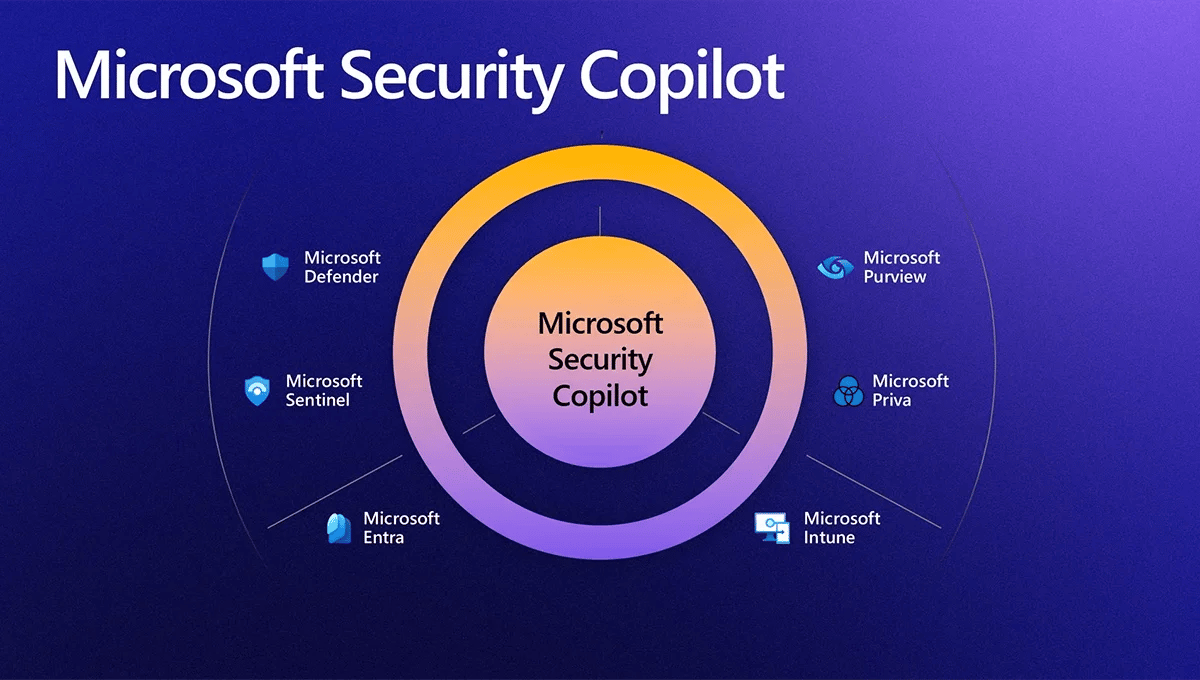
Copilot for Security provides a natural language, assistive copilot experience. Copilot for Security helps support security professionals in end-to-end scenarios such as incident response, threat hunting, intelligence gathering, and posture management.
Designed with integration in mind, Copilot for Security offers a standalone experience and also seamlessly integrates with products in the Microsoft Security portfolio. Copilot for Security integrates with products such as Microsoft Defender XDR, Microsoft Sentinel, Microsoft Intune, and other third-party services such as ServiceNow. For more information, see Copilot for Security experiences.
The solution leverages the full power of OpenAI architecture to generate a response to a user prompt by using security-specific plugins, including organization-specific information, authoritative sources, and global threat intelligence. By using plugins as data point sources, security professionals have wider visibility into threats and gain more context, and have the opportunity to extend the solution’s functionalities. For more about plugins, read Manage plugins.
Looking Ahead
As AI continues to evolve, its role in cybersecurity will become even more prominent. However, it's essential to recognize that AI is not a silver bullet; it's just one piece of the cybersecurity puzzle. Effective cybersecurity requires a holistic approach that combines AI-driven technologies with human expertise, robust policies, and ongoing training and awareness efforts.
In conclusion, AI is revolutionising cybersecurity by enhancing threat detection, streamlining incident response, and bolstering overall resilience against cyber threats.
By harnessing the power of AI, organisations can stay ahead of cybercriminals and protect their digital assets in an increasingly hostile online landscape.
Share Link